Production Data Contain Sensitive information should not be shared with unauthorized people this data contain financial , Account Number , ATM passwords … , Most of the company contain Developers team to support applications and modify the code as they need it, But the developers need data to test the code, How to get this data, This the Question ?
I seen lot of Company Use Production Data on development database/Test Database because it’s great for testing,really easy and No cost for doing this but is this right ? My View On this Topic No production data is allowed on the development. There’s lot of point to discuss to proof exactly what i mean and if it’s necessary to use it then hide it with multiple ways i will talk about it.
There is a lot more chance that the data may be compromised,This data should be removed and sanitized to make it anonymous / De-personalized.I read lot of articles every article explain something different for example This article support using Prod Data. after reading this blog ask yourself one question how the production make job easier ? by let developer/unauthorized people looking to customer Data !!!! Different point of view Customer want their data to be secure and the employees want to test the code and something easy and real to use.
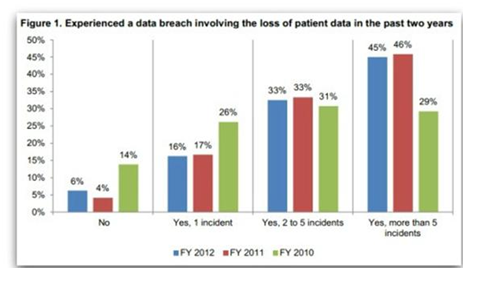
Check this The Ponemon Institute has come out with some interesting (and scary) data on data security during development and testing.
This chart shows what Breach of data. It shows a lot of sensitive data such as card holder data, customer data, credit card information and business confidential information.
Personally I prefer to use a subset or dummy data use Red-Gate Data Generator,
There’s lot of security issue can be lead by Using Prod data for testing/development such as severely compromise its confidentiality, even leading to legal action.
Take this example Hannaford Brothers,In March, the Maine-based Hannaford Brothers grocery store chain
announced that 4.2 million customer card transactions had been compromised by the hackers. More than 1800 credit card numbers were immediately used for fraudulent transactions.
after all this examples is it Ok to use Prod Data On test ? Do you have a legitimate reason? do you have
Security,Encryption, Firewalls, Breech Detection , Include to that There’s difference Security Rules On prod data and Test Data , Production database For authorized People, Privacy, Auditing, Roles , Privileges lot of conditions to access it. on the other hand Development data Frequently wide open,Dozens of employees have access, Access from many to unlimited places, Home access And you still Want to use Production Data ? Do you programs care or know the difference ?
Some Rules you have to follow :
- Make your employees aware of the policies and procedures.
- If it is possible to not use production data, take that option.use alternate ways of testing scenarios.
- Ensure that production data is masked or scrubbed when it is moved out of the production environment.
if it’s necessary to use your Production Data Then Do it right by scrambling (Scrambling is the function of replacing a character (or byte) of data with a different character (or byte) of data) Oracle Provide you with solutions to do that called data masking By write your own function that will Scramble data for you.
another option could be use is encryption (Encryption is a series of algorithms used to encrypt data into nonsensical characters (not in the English alphabet)). There’s Another way you can hide production data NULL’ing Out,Substitution, Gibberish Generation ….
Finally Using live data in non-production is either illegal or expensive. For the companies using it illegally, it’s only a matter of time before somebody slips up and the practice is discovered
Read Ponemon Institute Report