ORA 600 “internal error code, arguments: [%s], [%s],[%s], [%s], [%s]”
and you should it’s different Oracle errors , Because when you see this error then it’s indicating for bugs, the above is general description for the error the first characterset / Number is is used with database version to identify the problem by oracle support. and maybe you will find related document on https://support.oracle.com.
When you face this error you should check the below document searching for some Notes/Patch could help you :
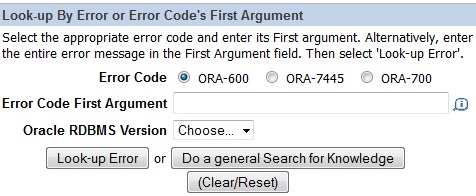
Note 600.1 ORA-600/ORA-7445 Lookup tool
You need to Choose database version ( 4 digit ) and First argument in the error, also for more information how to use this tool :
Note 1082674.1 : A Video To Demonstrate The Usage Of The ORA-600/ORA-7445 Lookup Tool [Video]
Notice when you check the alert log and see this error, a trace file is generated and an entry is written to the alert.log with details of the trace file location, trace file provide you with more information about the error that could help you to solve it. you can check the below document how to use trace file :
Note 453125.1 11g Diagnosability Frequently Asked Questions
Note 443529.1 11g Quick Steps to Package and Send Critical Error Diagnostic Information to Support[Video]
Most Common Reason for ORA-00600 File-Corruption, Failure in Hardware, I/O , or memory, to solve this error you need to do some steps before Open Services Request :
- Check Alert Log .
- Don’t forget to look at the Ora-00600 Tools.
- If you find any Notes related to your problem use it and read it carefully.
- The last option you could help is contact Oracle Support by open Services Request but provide the full information such as:
- alertlog for database.
- Traces.
- If any change happened lately included with SR.
- I post About RDA it’s useful to use it when you open SR.
Thank you
Osama Mustafa